The Story
Picture this:
A simple typo. Just one missing bounds check in a sea of OpenSSL code… and it became a digital knife that could slit open the encrypted heartbeat of the internet.
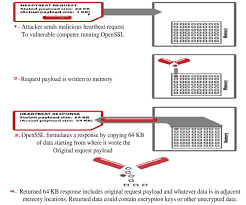
In early 2014, security researchers discovered something that felt unreal — a flaw that let attackers silently siphon memory straight out of servers. Not files. Not logs. Memory. Raw, unfiltered thoughts of machines.
Imagine walking up to a bank vault and asking, “Can you just… hand me whatever’s inside?”
And the vault just shrugs and hands you cash, keys, blueprints — whatever happens to be lying around.
That was Heartbleed.
Servers leaked passwords, session cookies, private keys, and personal data — and had no idea it was happening.
It didn’t scream.
It didn’t alarm.
It didn’t log a thing.
It just bled.
The Aftermath
Heartbleed affected:
- The U.S. government
- Banks
- Healthcare providers
- Fortune 500s
- VPNs
- Major websites including Yahoo!, Tumblr, and more
It forced the biggest emergency patching event in internet history, and forever changed how we audit open-source libraries.
Global Impact
- Exposed the fragility of internet-wide encryption
- Sparked the rise of bug bounties
- Led to funding initiatives for open-source security
- Proved that one small bug can impact 500+ million users