RSA wasn’t supposed to be vulnerable.
They were the company that made security tokens for militaries, governments, and Fortune 500s. Their job was to guard secrets — not lose them.
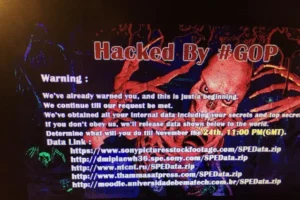
The Sony Pictures Hack: The Movie That Started a Cyberwar (2014)
Employees panicked as machines shut down, phones died, and entire servers started erasing themselves. Backup drives were overwritten. Render farms collapsed. Years of unreleased scripts,



