The Story
Stuxnet wasn’t written like malware.
It was written like a surgical weapon.
Somewhere in a classified facility, engineers from two allied nations built code the way precision machinists build instruments — carefully, quietly, and with deadly accuracy.
Their target: the Natanz nuclear enrichment facility in Iran.
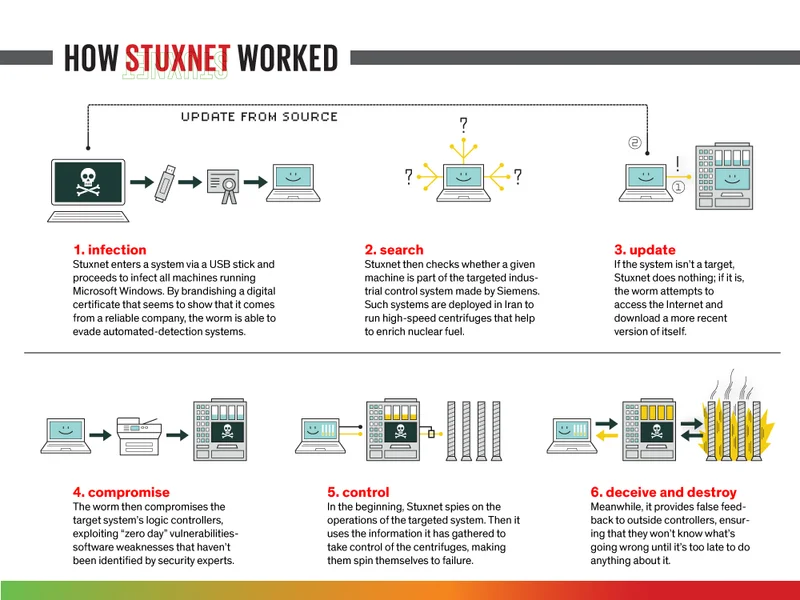
The Iranians believed their centrifuges were secure — isolated from the internet on an air-gapped network.
But Stuxnet didn’t need the internet.
It needed a USB stick.
Once inside, Stuxnet studied the environment, mapped it, and waited until the exact right moment. Then it rewrote the PLC instructions controlling uranium centrifuges — making them spin faster, then slower, then violently off balance.
To Iranian engineers, everything looked normal.
Their screens displayed perfect values.
Their logs showed no errors.
But machines were tearing themselves apart.
This was the first known piece of malware designed to cause physical destruction.
Aftermath
- Over 1,000 centrifuges were destroyed
- Iran’s nuclear program was set back years
- The world realized cyberweapons were now as real as missiles
Global Impact
- Nations accelerated offensive cyber programs
- ICS/SCADA security became a global priority
- Cemented the age of digital warfare